This blog post is the culmination of our Securing the Supply Chain series. In our second blog post Securing the Supply Chain - Meeting NISP SP 800-171 R2 we provided information on meeting compliance with DFARS (Defense Federal Acquisition Regulation Supplement) contracts clause 252-204-7019, which triggers your compliance with NIST 800-171 R2 by uploading your self-assessment, System Security Plan, and any Plan of Accreditation & Milestone (POA&M - Plan Of Actions and Milestones) to SPRS (Supplier Performance Risk System) system. Our initial blog covered what the government wants you to protect, the interim rule, Cybersecurity Maturity Model Certification (CMMC) levels, and how to get started. In this blog we start the journey toward meeting compliance with CMMC. We begin with first meeting compliance with NIST SP 800-171 R2, the latest self-assessment and self-attestation standard. Ultimately, over the next five years (by 2026), you will be required to meet DFARS contract clause 252-204-7021, which will trigger compliance with appropriate level of CMMC compliance.
The Cybersecurity Maturity Model Certification (CMMC) is a compliance framework for Defense Industrial Base (DIB) contractors to safeguard intellectual property of United States. DIB contractors must properly safeguard, disseminate, and destroy Controlled Unclassified Information (CUI). As a DIB contractor, you will need to comply with the appropriate CMMC maturity level to renew a contract, compete for a new contract or receive an award of a contract. In this blog we give you the information you need to meet CMMC compliance.
CMMC Goes Beyond NIST 800-171 R2
Here are the major differences between NIST 800-171 R2 and CMMC.
- CMMC is a certification that requires a third-party assessment by a certified assessor, whereas NIST 800-171 R2 requires only a self-assessment.
- CMMC has maturity levels and, based on the type of CUI you must protect, there are five maturity levels.
- CMMC certification level requires meeting the requirements of both process AND practice.
- CMMC requires a visit by certified assessor to your place of business.
- CMMC requires continuous monitoring and continuous compliance.
CMMC Model and Guides
To understand the CMMC model and guides for the assessment you will want to refer to this guide. The CMMC framework consists of both process and practices (controls, tasks) organized into set of domains that map across five levels.
CMMC Model Framework
Simplified Hierarchical View
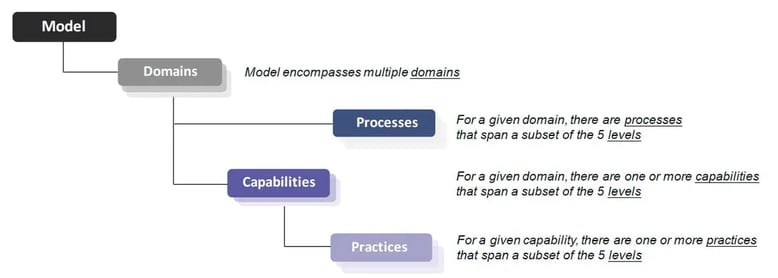
http://www.securityuniversity.net/cmmc-cybersecurity-maturity-model-certification.php
CMMC Assessment Overview
The self-assessment work done to meet 800-171 R2 does count towards CMMC. As a matter of fact, 110 controls apply toward CMMC level 3. But now that you must meet CMMC compliance and have a certified auditor visit your location to assess your compliance posture, you will want the following guidelines to help you be successful. Below is recommended assessment lifecycle:
- Baseline – Because you will have to write policies and have an auditor assess your controls, it is highly advisable for you to hire a consultant to perform a gap assessment to baseline your environment. This will allow you to focus on process and practices to implement before scheduling the auditor’s assessment.
- Remediation - Any gaps must be methodically remediated with the implementation of safeguards to meet practices (controls), processes and having documented policies. Gathering of body of evidence for each control is needed. If you need assistance, there are certified organizations and consultants for hire. You can find these resources at the CMMC Marketplace.
- Operationalize – It is advisable to have the newly implemented policies, process, practices in place for 2-3 month before you have an assessor audit your environment. This will allow you work out any kinks, get feedback from employees and live your new normal.
- Assessment – Having a consultant assisting you prepare for an assessment is advisable. Before the audit of your environment is initiated, you should have the body of evidence ready. If you need help hiring Certified Third-Party Assessment Organization (C3PAO), please see the CMMC Marketplace or ask for a referral from your consultant. The C3PAO assessment team will review content to ensure that you demonstrate sufficient adoption of the applicable practices and processes. Once completed, the certification is good for 3 years.
- Maintenance – continued compliance with all applicable policies and processes is required. Your organizational culture must continue to protect sensitive data.
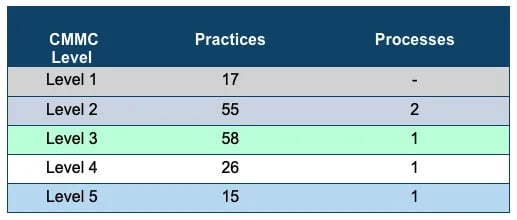
CMMC Levels, Practices and Processes
Practices are aligned to set of capabilities in a domain. The CMMC model aligns maturity processes, cybersecurity practices and levels of information to be protected. A process is how an organization ensures effective implementation of practice activities. This model covers safeguard of Federal Contracts Information (FCI) at level 1 to safeguard against sophisticated persistent threats at level 5.
CMMC Domains
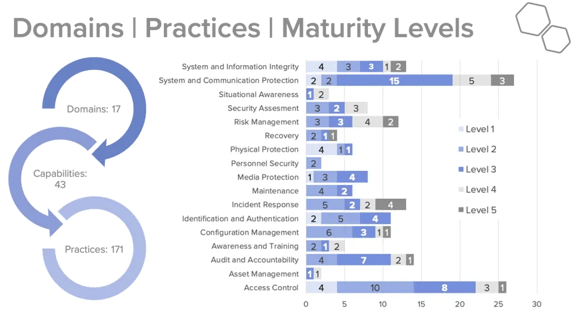
CMMC has 17 Domains, belonging to 43 capabilities associated with 171 practices across five CMMC levels. CMMC levels build on each other, so practices and process met for level 1 and level 2 apply towards level 3. Note that Level 2 is an intermediate step between Level 1 certification and Level 3 certification. The majority of the practices (110 of 171) originate from the safeguarding requirements and security requirements specified in DFARS Clause 252.204-7012, which triggers compliance with NIST 800-171 R2.
The chart below also shows the distribution of practices across level belonging to a domain.
CMMC and Protecting CUI
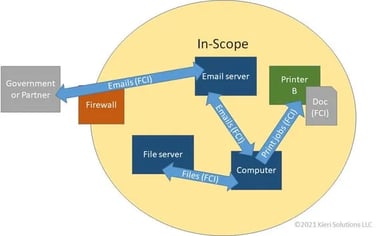
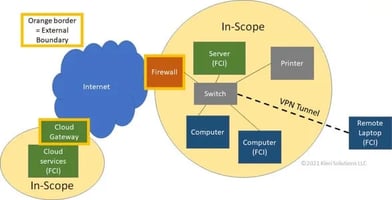
When protecting intellectual property, it must be protected while being processed by an application, while at rest (in storage), and during transit (transmission to a third party). Depending on the size of your on-premises environment, and how much of it is dedicated to government work, you will have to make some decisions about hardware and software, and whether to own or lease. The systems that are used for government work -- those systems that process, store and transfer CUI data -- are consider “in scope” or part of the boundary. The systems within the defined boundary are the ones that will be assessed for compliance. Defining scope is particularly important.
This example is showing how the data flows between the systems in scope (processing, transmitting or storing CUI.) if you have one central location.
|
This example is showing how the data flows between the systems in scope (processing, transmitting or storing CUI.) if you have one central location.
|
CMMC Audit Preparation
|
|
This example is showing how the data flows between the systems in scope if you have remote locations.
|
Systems remote locations
|
CMMC Assessment Preparation
These are the steps to prepare for your CMMC assessment.
- Identify where your sensitive data exists and who has access.
- Systems hosting FCI/CUI data
- Identify your data systems
- Identify connector systems
- Identify systems with security roles
- Who has access to FCI/CUI, and who is responsible for this data?
- Data flow diagram to show transmission of sensitive data between systems
- Diagram must show there is functional way to move sensitives data into and out of in-scope systems
- Must show data movement and protection at each step
- Network Diagrams - Documenting systems in a network diagram are an effective way to demonstrate scope to your assessor.
- Organizational Diagram and facility diagrams are further proof that you have good grasp of controlling the flow of the sensitive data. These diagrams do not be detailed.
CMMC Assessment Resources
Having a good consulting organization can be greatly beneficial to help your organization prepare for assessment. If you decide to tackle this by yourself, there are number of guides and resources available to assist. The CMMC only explains what practices a company must implement, it does not explain how the implement them, this is where a consulting firm or a cybersecurity firm can add value.
Policies - Given that you will have to document policies, here are some guidelines to creating a policy:
- Clearly state purpose
- Clearly define scope (enterprise wide or specific system)
- Defined roles and responsibilities of activities/practices covered
- Procedure to carry out and meet the intent
- The regulatory guidelines policy addresses
- Senior management’s signature(s)
Tools - There are number of compliance management applications that I have researched and narrowed down to couple that are great to help you organize your documentation and one has policy templates to help you draft a policy. Please reach out to me and I would be happy to share the vendor names.
Guides – If you are planning to prepare for the assessment, here is where you find guides to help you navigate assessment preparation.
Journey to CMMC Conclusion
According to the CMMC Accreditation Board and the Department of Defense, approximately 70% of the contractors in the Defense Industrial Base will require either Level 1 to protect FCI or Level 3 certification to protect CUI. As a DoD contractor, you are helping secure the supply by protecting the information entrusted to you by government of the United States. By meeting the compliance requirements of CMMC, you are also improving the security posture of your organization’s information systems. You should proudly share this certification achievement with your shareholders and your customers, this indicates that your organization value being a government contractor and supporting America.
GOVFTP Cloud is your compliant solution for secure exchange of FCI and CUI files. We wish you all the best on your CMMC journey. The Sharetru team is here to help in any way we can. If you are interested in a demo or have additional product questions schedule a demo today!







