This blog post is a continuation of The CMMC Basics where we covered what the government wants you to protect, the interim rule, Cybersecurity Maturity Model Certification (CMMC) levels, and how to get started. In this blog we start the journey toward meeting compliance with CMMC. We begin with first meeting compliance with NIST SP 800-171 Revision 2, the latest self-assessment and self-attestation standard.
The United States government is challenged with securing the supply chain to reduce theft of intellectual property, collection of intelligence by foreign adversaries, and introduction of counterfeit products. The Department of Defense (DoD) must assure that the mission of the warfighter is not compromised, furthermore, the research and development, ideas , and product specifications are not stolen. As we become more of an interconnected world, this will be more challenging, so you must take steps to ensure that you are keeping your information safe as a Defense Industrial Base (DIB) vendor. If you are among the over 300,000 hardworking vendors supporting the DoD — be proud and be ready to do your part in helping America’s continued prosperity.
In February, we hosted a webinar about the Cybersecurity Maturity Model Certification (CMMC) and DFARS Compliance. During the Q&A we received several questions regarding more in-depth information about the journey to CMMC compliance. So, we decided to put together a series on the Cybersecurity Maturity Model Certification and start with the basics!
DFARS and NIST 800-171 Revision 2
Since 2017, the DoD has required DoD DIB vendors to comply with contract clause DFARS 252.204-7012. When you are compliant there, the next requirements are triggered for NIST SP 800-171 Revision 2 Protecting Controlled Unclassified Information (CUI) in Nonfederal Systems and Organizations. Given that this requirement to meet DFARS (clause 252.204.7012) has been in place since 2017, the number of contractors not in compliance is staggering. Therefore, starting December 1, 2020, the DOD began taking a “trust but verify” approach (we covered DFARS 252.204-7019 in our CMMC Basics blog post) by having contractors upload the self-assessment and self-attestation results (System Security Plan (SSP) and Plan of Action & Milestones (POA&M)) into a DoD system, Supplier Performance Risk System (SPRS) or via email to webptsmh@navy.mil.
The Self-Assessment
When complying with DFARS 252.204-7019, you must conduct a self-assessment of compliance with NIST SP 800-171 Revision 2 and receive a score. The maximum score is 110 points. The NIST SP 800-171 A provides a score for each control, so you must understand the scoring system. Each control has a scoring weight. Fully addressing a control gets a score of 1. Not meeting a control requirement is given a score of 0 or even a negative score. A perfect score is 110 but you can achieve an overall negative score. The SPRS is the single source for contracting officers to view your compliance information to consider your company for an award. Also, if you are a subcontractor, you should communicate with your prime contractor about CUI and program requirements.
DoD Assessment Methodology
NIST 800-171 and NIST 80-171A
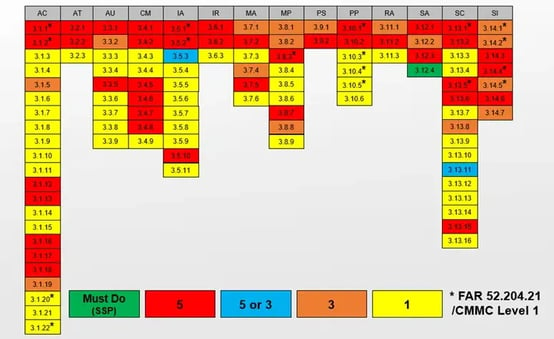
https://www.totem.tech/how-to-generate-and-report-your-dod-self-assessment-score/
The 14 Security Control Families
For NIST 800-171 Revision 2 there are 14 control families (a.k.a. categories) of security requirements, with a maximum of 110 controls that need to be self-assessed. At the time of self-assessment, you must generate a System Security Plan (SSP) to show how your company complies with the standards. If there are controls that are not met, you simply document them on a Plan of Actions and Milestones (POA&M) form, with a timeline of when you will meet compliance. Templates for SSP and POA&M can be found on the NIST website.
The image below represents the people, process, and technology involved for a self-assessment.
NIST 800-171 Revision 2 Summary
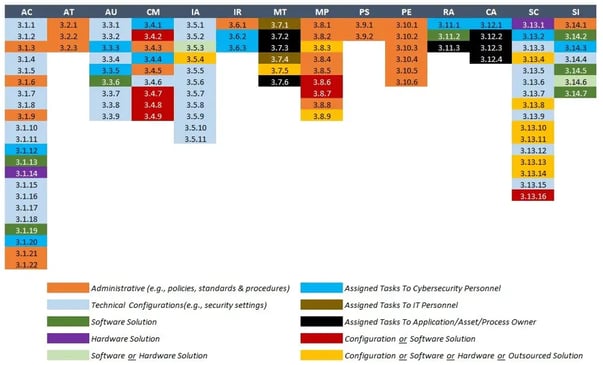
https://www.complianceforge.com/reasons-to-buy/nist-800-171-compliance/
NIST 800-171 Revision 2 Requirements and CMMC
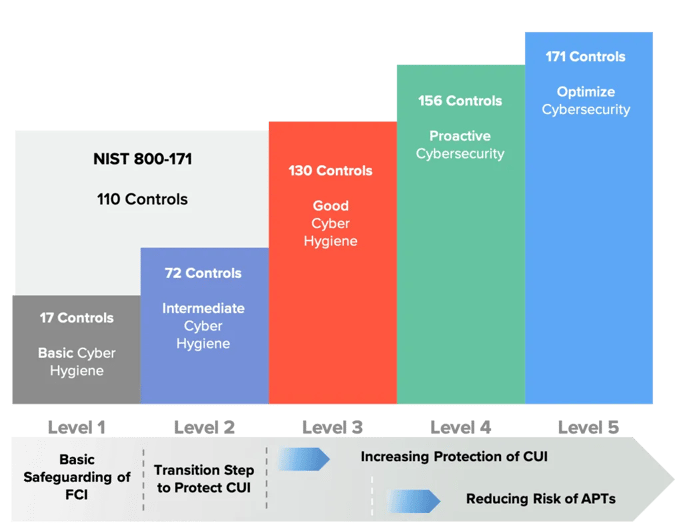
Complying with both NIST 800-171 Revision 2 and DFARS 252.204-7019, you are well on your way to meeting CMMC level 3 compliance. We will go into more details about CMMC in our next blog. Scoring and reporting to SPRS is your top priority. Here is list of documents you will need:
- NIST SP-800-171 Revision 2 requirement, SSP and POAM&M templates for self-assessment
- NIST SP-800-171 A Assessing Security Requirement for CUI
- NIST SP-800-171 A Control Scoring document
- SPRS - Instructions to upload assessment report and access to SPRS
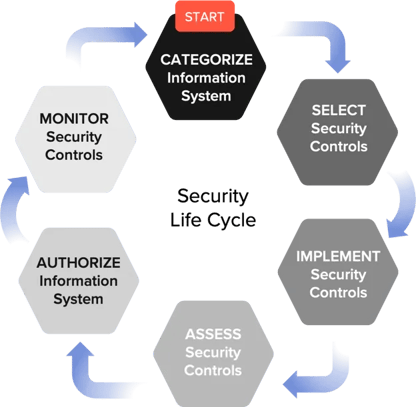
If you missed our CMMC and DFARS Webinar in February you might remember seeing this graphic! If you were unable to attend but would like to access the webinar on-demand you can! Check out the webinar here! It is important to note that if you are working towards a contract award, once you submit your self-assessment in SPRS, it will take 30 days from date of submission to post a score. You should account for such lead time. Also, if your company is not 100% compliant, a POA&M must be included. The self-assessment is good for three years (or sooner if required by a contract).
Whatever you do, be as honest as possible with your self-assessment. DO NOT make a false claim, as in claiming to comply when you do not. False statements of compliance face prosecution under the False Claim Act. The DoD has used the False Claim Act to crack down on contractors. The Defense Contract Management Agency (DCMA) is auditing contractors for NIST 800-171 compliance. If you are found guilty of false claim, you may be barred from doing business with the U.S. Government along with other financial penalties.