The United States of America is increasing attention on cybersecurity to ensure the prosperity of the American people. Public and private entities must secure systems, and networks from adversaries with malicious purpose. In this effort to secure Federal networks, one of the areas of focus for the government is the Federal Supply Chain and strengthening the security of United States Government contracting systems.
The global nature of the Internet allows all countries to participate in communication, commerce, and free exchange of ideas – allowing for true prosperity. Access to something as powerful as the Internet presents opportunities for outside nations to conduct espionage, steal intellectual properties, cybercrimes, and remotely attack critical infrastructure.
A few weeks ago, we hosted a webinar about the Cybersecurity Maturity Model Certification (CMMC) and DFARS Compliance. During the Q & A we received several questions regarding more in-depth information about the journey to CMMC compliance. So, we decided to put together a series on the Cybersecurity Maturity Model Certification and start with the basics!
Why the Government Wants Your Systems & Networks Secured
Today, federal government contractors are using systems to store sensitive information. These systems must be secured with the required compliance controls. A federal government contractor could be a business that is part of the private sector, a research and development facility, or a university performing research.
Without adequate security, government adversaries, or state funded actors, can use complex strategies to gather small pieces of information that may add up to a complex zero-day attack. These small pieces of information could help them reverse engineer a piece of software, development timeline, machine parts, pieces of the U.S. Government supply chain or critical infrastructure. Because of our continued digitalization, these cyber threats bring into question the integrity of our war fighter readiness, while presenting a larger risk to the United States government with each passing year.
Risk is shared by both the private sector and the Federal government. We must use a risk-management approach to mitigate vulnerabilities. As a defense contractor, you are asked to do your part by having controls in place to safeguard systems that store sensitive government information.
What the Government Wants You to Protect
It is important to understand the types of information you need to protect to ensure you make the best decisions for your organization. In 2007, the federal government established the Defense Industrial Base (DIB) Cybersecurity Task Force. The U.S. Government is asking you to protect Controlled Unclassified Information (CUI). As of 2015, DoD contracts require Safeguarding Covered Defense Information (CDI), a type of CUI, and Cyber Incident Reporting with DFARS clause 252.204.7012. CDI is typically stored in Covered Contractor Information Systems. These systems store, process, generate, transmit, or access DoD-related Controlled Unclassified Information (CUI).
DFARS was put into effect in 2016 as a way to help government contractors better protect sensitive data flowing in and out of their organization. Since then, the United States has continued to put stronger security regulations in place to promote cybersecurity, like the standards from the National Institute of Standards and Technology (NIST). It is under the DFARS clause that contractors must apply the cybersecurity requirements of NIST SP 800-171. Contractors and subcontractors with access to covered defense information have been self-certifying to comply with DFARS clause 252.204.7012 since 2017.
CMMC Timeline
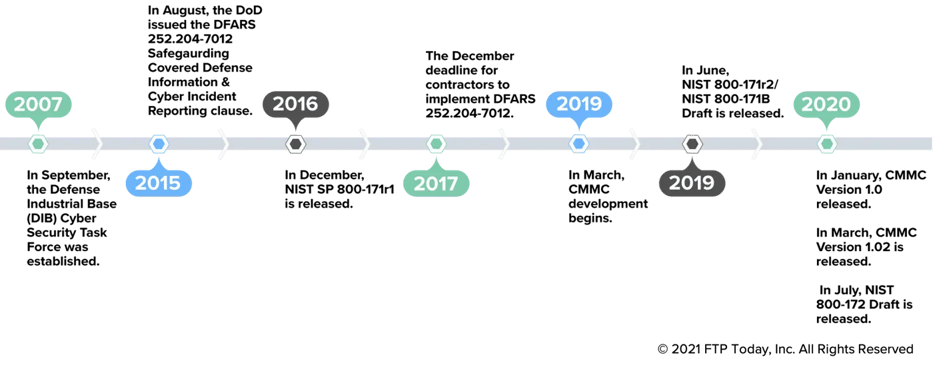
Going forward, the government will trust your self-certification, but will also verify that you are compliant. Since late 2020, the results must be reported to the DoD database Supplier Performance Risk Systems (SPRS). Your assessment is good for three years.
If you are interested in a deeper dive on how to prepare for DFARS Compliance we have created a DFARS Preparation Guide. In addition, our Glossary of DFARS Compliance Terms may also be useful as you navigate your journey to compliance.
The Interim Rule
The interim rule for implementing the Cybersecurity Maturity Model Certification (CMMC) program that will eventually lead all DoD contractors to meet CMMC certification. Serving as the basis for the interim rule, DFARS 252.204.7012 triggers your compliance with NIST SP 800-171. We have presented the interim rule using a Crawl, Walk, Run approach.
Starting December 1, 2020, the CMMC interim rule will be rolled out and implemented over five years, after which CMMC will fully apply to all DoD solicitations and contracts (except COTS and Micro Purchases).
Interim Rule Timeline
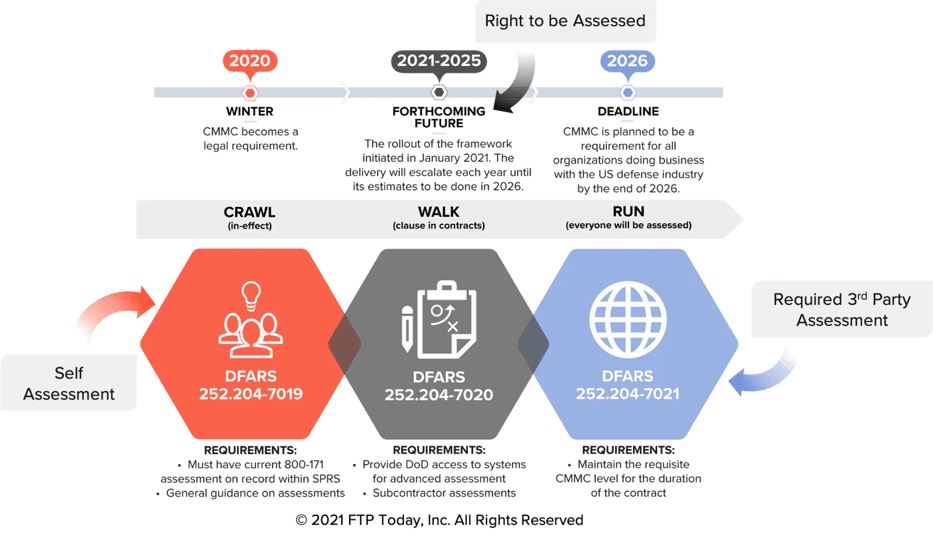
- Crawl – DFARS 252.204.7019: Notice of NIST SP 800-171 DoD assessment requirements. After December 1, 2020, all DoD contractors are required to upload NIST SP-171 self-assessment data to the Supplier Performance Risk Systems (SPRS) to be considered for an award.
- Walk – DFARS 252.204.7020: Notice of NIST SP 800-171 DoD assessment requirements. This requires a contractor to provide the government with access to its facilities, systems, and personnel when it is necessary for DoD to conduct or renew a higher-level assessment.
- Run – DFARS 252.204.7021: Cybersecurity Maturity Model Certification (CMMC) is required for all solicitations and contracts, task orders or delivery orders (except for COTS purchase or micro awards). Contractors are required to maintain the CMMC level for the duration of a contract.
Doing business with the DoD means a commitment to Cybersecurity that is based on a trust but verify process. By 2026, all certifications will be done by a DoD Certified Third-Party Assessment Organization (C3PAO).
Cybersecurity Maturity Model Certification (CMMC) Levels
The CMMC model consists of five maturity levels and 171 cybersecurity practices mapped across these maturity levels. This structure helps to institutionalize cybersecurity activities, ensuring that they are consistent, repeatable, and of high quality.
The CMMC practices provide a range of mitigation across 5 levels. Starting at Level 1 with the basic safeguarding of Federal Contract Information (FCI). Moving into the broad protection of Controlled Unclassified Information (CUI) at Level 3. Reducing the risk of Advanced Persistent Threats (APTs) at Levels 4 and 5. Most contractors will need to meet either Level 1 (Basic) or Level 3 maturity levels (protect CUI).
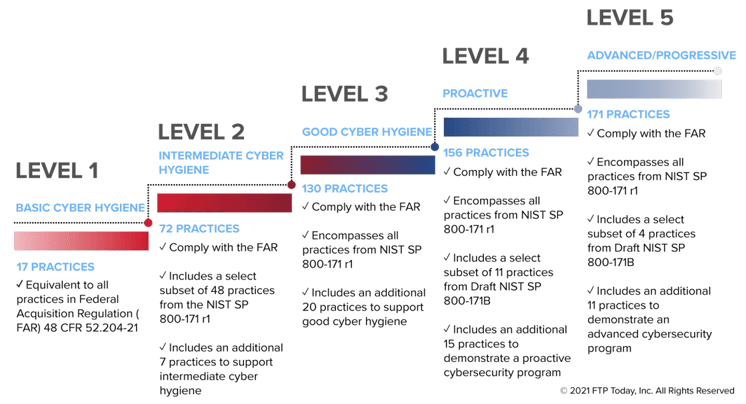
The CMMC framework is coupled with a certification program to verify the implementation of these important cybersecurity processes and practices.
How to Get Started & Be Prepared
You should be ready to do your part in helping secure the supply chain by protecting Covered Defense Information. Preparing for CMMC is a straightforward process thanks to the DoD using NIST 800-171 as the foundation. Determining the priority, timing and steps necessary to achieve CMMC is not as complicated as it seems. Here are some measures to get you started.
Step 1: Assess your current operations for compliance with NIST 800-171.
Step 2: Document your Plan of Actions & Milestones (POAMs).
Step 3: Document your System Security Plan (SSP).
Step 4: Implement the required controls.
Step 5: Maintain compliance.
Meeting and keeping compliance will not be easy nor cheap. So, it is best to have a good team to help you. For small businesses there are several resources available based on your specific approach.
- Self Help/DIY – Resources available through Project Spectrum, a Small Business Cyber Mission Accelerator.
- SaaS/Apps – There are a variety of Applications and Software services that provide compliance management on your journey to CMMC accreditation.
- Consultants – The CMMC Marketplace has certified resources to guide you through the accreditation process.
GOVFTP Cloud is your compliant solution for secure exchange of FCI and CUI files. We wish you all the best on your CMMC journey. The FTP Today team is here to help in any way we can. If you are interested in a demo or have additional product questions schedule a demo today!





