In the modern age, cybersecurity has become a serious priority for organizations operating in both the public and private sectors. Government entities prioritize cybersecurity to prevent foreign actors and third parties from accessing state secrets. Corporations and other businesses prioritize cybersecurity to prevent ransomware, the loss of proprietary information and trade secrets, and generally to secure any information and files they store and share.
What is SOC 2 and where does it fit within the emerging cybersecurity universe that’s growing more important with each passing year? SOC, an acronym for “System and Organization Controls,” is a cybersecurity risk management reporting framework that includes different levels for different types of organizations — SOC 2 is the second level of the framework designed for service providers.
The SOC framework and SOC 2 requirements for service providers have become a universally accepted standard for securing information, data, and files. At Sharetru, we are SOC 2 certified with Advanced Security and Compliance Enablement Add-on considered in scope. This is one of the best ways to ensure we’re securing our users’ data and files while minimizing the risk of outside threats. See below for more details on the SOC framework, SOC 2 compliance, plus what it means for your organization.
Where Did the SOC Framework Originate?
The American Institute of CPAs (or AICPA) designed the SOC framework in response to growing cybersecurity risk and the increasing relevance of cybersecurity to organizations in a wide variety of industries. The framework creates a structure for organizations to clearly communicate how they are detecting, preventing and responding to cybersecurity threats. Furthermore, the framework also creates a process for CPAs to examine, audit and report on any organization’s cybersecurity efforts as they relate to the framework. This provides third-party validation for an organization’s risk-mitigation efforts.
The AICPA first announced the SOC framework in 2011 as a structure for enabling “CPAs to report on security, availability, processing integrity, privacy or confidentiality.” The framework has evolved over time in response to the shifting cybersecurity needs of organizations in different sectors. Then, in 2017, the AICPA established the Trust Services Criteria which is used in attestation and consulting engagements for the evaluation and reporting on the controls related to the privacy of information (and the systems the information is stored on).
Three Types of SOC Reporting
The SOC framework neatly divides organizations into three different reporting types. These three different types come accompanied by different requirements. Here’s a look at the three reporting types, the reports’ intended audiences, plus the benefits of SOC compliance at each one:
- SOC1 (Entities): SOC 1 was designed for entities needing to communicate reports to management, board members, investors, regulators, and analysts. SOC 1 provides transparency into cybersecurity risk management efforts, improves communication, and it enhances confidence while primarily being focused on an organization’s financials.
- SOC 2 (Service Providers): SOC 2 controls were designed for service providers needing to communicate reports to chief information security officers, business unit managers, vendors, accounting and internal audit professionals, etc.
- SOC 3 (Supply Chain): SOC 3 was designed for supply chain participants to communicate reports to many of the same audiences as SOC 2: chief information security officers, business unit managers, vendors, etc. SOC 3 provides details on how an organization manages supply chain-related cybersecurity risks. Similarly, when you evaluate SOC 2 vs SOC 3, you’ll find that SOC 3 includes all of the benefits of SOC 2 and then some.
Sharetru maintains SOC 2 compliance and certification, and similarly to other organizations can provide these reports to our clients with a unilateral NDA in place.
The Benefits of SOC Reporting
The SOC framework wasn’t intended to create tasks for organizations to complete. Rather, it was initially created as a public service that would actually create benefits for the organizations that followed it. The SOC framework was designed to:
- Create Common Criteria: The SOC framework standardizes cybersecurity reporting, creating common criteria for disclosures and regular assessments of effectiveness.
- Lessen Communication and Reporting Burdens: The relatively streamlined nature of SOC reporting is meant to lessen the communication and reporting burden on organizations. While there are strict reporting requirements, these requirements are as minimal as possible to allow organizations to focus on other important aspects of their businesses.
- Provide Useful, Relevant Information to Interested Parties: SOC reporting should include useful and relevant information that can quickly and easily be shared by organizations with any interested parties: prospective users, board members, senior management, etc.
- Outline Best Practices: The SOC framework provides best practices that leaders can adapt and implement in the best way for their organizations. SOC requirements are flexible, allowing for comparability without constricting organizations to a single process or approach.
- Scale for Organizations of Different Sizes: The SOC framework can be adopted by a small business just as easily as a large, multi-national corporation.
- Evolve to Meet Real-Time Needs: As noted above, the SOC framework is constantly evolving to respond to the latest cybersecurity threats. It’s now been 10 years since the SOC framework first launched. Cybersecurity threats have evolved in the past decade, and the SOC framework has evolved to meet them head-on.

How Organizations Approach SOC 2 Compliance
Sharetru maintains SOC 2 compliance and certification as an essential part of our operations. As a service provider to organizations large and small, operating in both the public and private sectors, we help to ensure that end users avoid cybersecurity threats. Having safeguards in place to protect user data from cybersecurity threats is the goal, and a service provider must meet a list of controls and objectives. Here’s a look at the SOC 2 compliance checklist that includes the 11 components of cybersecurity:
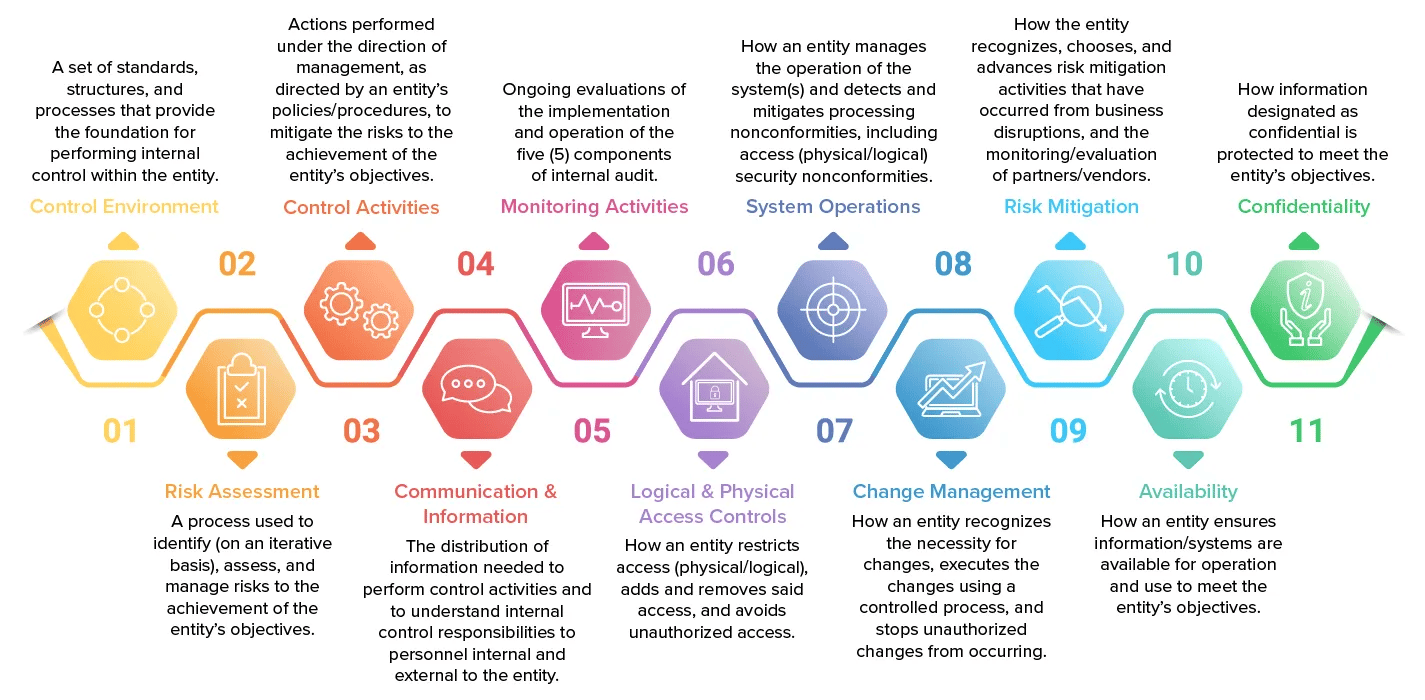
1. Control Environment
SOC 2 compliance asks service providers to create the right control environment for reducing cybersecurity risks. Creating an effective control environment includes commitments like:
- Allowing boards of directors to independently oversee organizational management.
- Empowering management to create reporting lines, structures, authorities and responsibilities that support SOC 2 objectives.
- Committing to the recruitment and retention of team members who can support SOC 2 objectives.
- Holding team members accountable for the successful completion of their responsibilities in support of SOC 2 objectives.
2. Risk Assessment
The SOC 2 framework is meant to be proactive (rather than reactive) to cybersecurity threats. That’s one reason why risk assessment is such an important part of SOC 2 compliance programs.
Proper risk assessment includes creating clear risk assessment objectives, identifying and analyzing risks so that they can be effectively managed, considering the potential for fraud in risk assessments, and continually looking for changes to internal controls that will make cybersecurity protections more effective.
3. Control Activities
SOC 2-related control activities include technology controls. They also include policies and procedures for what is expected of team members in using those controls to lessen cybersecurity risks.
4. Communication & Information
Communication and information addresses how relevant cybersecurity information will be disseminated to internal stakeholders as well as our users. SOC 2 compliance requires a definition of what information is deemed relevant, and then processes for communicating that information both internally and externally.
5. Monitoring Activities
SOC 2 compliance also necessitates monitoring of internal controls and whether or not they are in place and functioning as intended. Secondly, effective monitoring of cybersecurity activities also includes a process for communicating any deficiencies in a timely manner to team members responsible for taking corrective action.
6. Logical & Physical Access Controls
How does an organization control both physical and logical access to systems? At Sharetru, we use security software, infrastructure, and architectures to secure information assets to align with SOC 2 requirements. We register and authorize new internal and external users before granting system access. We also restrict physical access to facilities and assets, while protecting against external threats, protecting against in-transit threats, and detecting/preventing malicious software.
7. System Operations
Systems operations in compliance with SOC 2 include five specific activities:
- Creating procedures for detecting and monitoring vulnerabilities.
- Monitoring anomalies that may indicate malicious activity, natural disasters or other threats.
- Evaluating security events to determine whether responses met our standards.
- Executing a pre-defined incident response program.
- Implementing systems for recovering from security incidents.
8. Change Management
The SOC framework is meant to evolve to best combat the latest and greatest cybersecurity threats. Compliance with SOC 2 means creating change management policies and procedures that help ensure our organization is always best positioned to prevent cybersecurity incidents. At Sharetru, we are always implementing the best infrastructure, data, software, and procedures to ensure the efficacy of our cybersecurity program.
9. Risk Mitigation
Effective risk management includes choosing risk-mitigation activities in response to business disruptions, plus assessing and managing any risk related to working with third-party vendors and business partners.
10. Availability
We strive to ensure that our system is available to users for operation whenever needed. We do this by managing capacity demand, managing infrastructure, and testing recovery activities should they be needed.
11. Confidentiality
Many of our users are storing and sharing files and information that are highly sensitive in nature. This requires us to ensure confidentiality in regard to how files and information are used, who has access to them, plus how they are protected at rest and in transit.
What SOC Compliance Means for Our Users
SOC 2 as developed by the AICPA has become the most acceptable framework for implementing effective, verifiable safeguards against cybersecurity threats. At Sharetru, we invested time, energy, and resources into developing and implementing controls so that we’re always SOC 2 audit ready. Because the SOC framework is so widely accepted as the standard in cybersecurity, our users can rest assured that we have in place the most modern and most effective cybersecurity protections available.
Some of our users inquire about ISO 27001 vs SOC 2. At Sharetru, we choose to comply with both frameworks. We adhere to both ISO 27001 and SOC 2 standards at the datacenter level, which gives our users industry-leading security for their files. Dual compliance with ISO 27001 and SOC 2 ensures that our users’ data is hosted in a secure, military-grade, government-authorized data center.
Security Control Implementation Made Easy
Sharetru offers the controls necessary to meet a number of compliance requirements for organizations that need an effective, secure FTP hosting provider. We offer affordable hosting plans that are quick to configure, allowing your organization to take advantage of new opportunities and scale into projects that require adherence to intensive compliance requirements — like SOC 2 and others.
Are you looking for a compliant FTP hosting solution? Get in touch with us for a brief demo and answers to all your questions about SOC 2-compliant FTP hosting.



