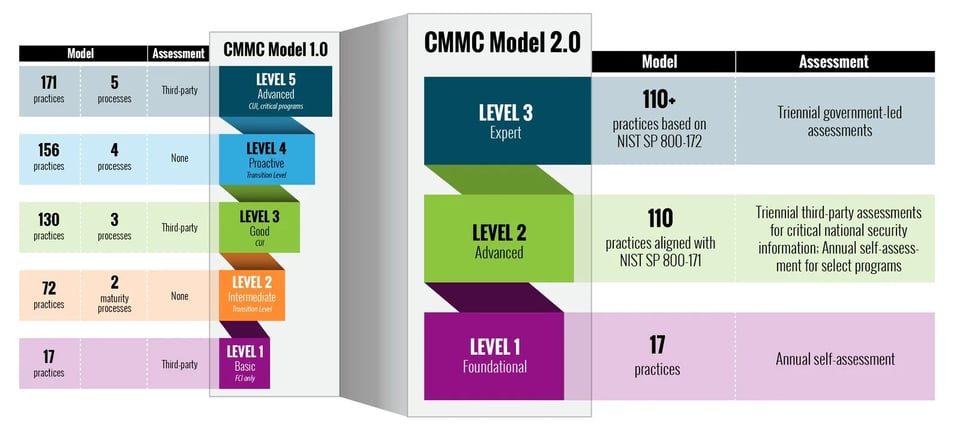
By now, all contractors that work with the U.S. Department of Defense should be fully aware of the Cybersecurity Maturity Model Certification (CMMC) 2.0 announcement from November 2021. The CMMC 2.0 announcement included updates to CMMC 1.0 that were designed to enhance cybersecurity protections for all entities in the defense industrial base, or DIB, and also streamline protections for contractors already utilizing the NIST 800-171 framework.
While the announcement of last November did provide a glimpse at what the DOD’s requirements might be in the future, Congress has yet to codify those requirements into a law to be followed. Unfortunately, that leaves contractors and others in the DIB in a limbo period where they know that new CMMC requirements are coming — but they don’t know exactly what those requirements will be.
We’ve written previously about the proposed CMMC 2.0 framework and what it might require of contractors. Now we’ll address what contractors and others in the DIB can be doing right now during this limbo period to set their organizations up for future success under CMMC 2.0 once codified by law.
While there’s a lot of confusion about what can be done presently, it’s best for DIB members to focus first on Level 1 requirements as outlined by the CMMC 2.0 announcement late last year. The following 17 specific practices are required for Level 1 compliance. They represent basic security hygiene that you can implement for your organization: limiting physical access to your facility and systems, securing storage and transport of data, and monitoring your systems usage are good places to start. Also, note that Level 1 compliance is the basis for Level 2 compliance.
Source: https://www.acq.osd.mil/cmmc/about-us.html
Access Controls
The first domain of CMMC 2.0 addresses access controls. Here’s a look at the access control-related capacities and practices that are required under CMMC 2.0’s Level 1.
Establish System Access Requirements
First and foremost, organizations must limit information system access to only authorized users, processes acting on behalf of authorized users or devices. The term “devices” includes other information systems in this context. The objective is to ensure that only authorized employees have access, and that access is disabled when an employee leaves the company.
Organizations must also limit information system access to the types of transactions and functions authorized users are given permission to execute. In short, all authorized users are then given authorization to do and access certain things necessary for their jobs.
Limit Data Access to Authorized Users & Processes
Beyond access requirements, organizations must also limit data access to authorized users and processes via two different practices.
First, organizations must verify and control or limit connection to and use of external information systems. This practice focused on controlling and managing the connection between the company network and the outside, as well as limiting personal devices accessing company networks and systems.
Second, organizations must control information posted or processed on publicly accessible information systems. Under this practice, organizations are limiting who can publish to your public systems and limiting the actual publishing of controlled unclassified information (CUI).
Identification & Authentication
After access controls, the identification and authentication domain is listed second under CMMC 2.0. Here’s a rundown of specific capacities and practices relevant at Level 1.
Grant Access to Authenticated Entities
Organization must only grant access to authenticated entities via two practices at Level 1. First, organizations must identify information systems and processes acting on behalf of users or devices. This is to ensure a user or process is identified before gaining access to company systems.
Second, organizations must verify the identities of all users, processes or devices as a prerequisite for allowing them access to the organization’s information systems. This practice is designed to ensure that password protection (or similar protections) are in place, and also that all default passwords must be updated to unique passwords.
Media Protection
Within the media protection domain, the only capacities and practices relevant at Level 1 are focused on sanitization of media. Here’s more on what’s required at Level 1.
Sanitize Media
Organizations are required to sanitize or destroy any information system media that contains federal contract information — or FCI. The media can be both physical (paper, CD, USB, etc.) and electronic information about your contract with government. The contract information is shared between you and the government official — it is not available to public. Sanitization of stored media or destruction is required before disposal or release for reuse.
Physical Protection
The third domain outlined by CMMC 2.0 is physical protection. Only one capacity (and its related practices) are relevant at Level 1 — limiting physical access. See below for more details on what’s specifically required.
Limit Physical Access
Organizations must limit physical access to all organizational information systems, equipment and respective operating environments to only authorized individuals. This includes:
- Escorting visitors and monitoring visitor activity.
- Maintaining audit logs of physical access.
- Controlling and managing physical access devices.
While FTP as conceived in 1971 did have security vulnerabilities, there are now encrypted file transfer protocols that layer on top of FTP the security needed for sensitive files. More specifically, FTPS and SFTP are options for organizations that need highly secure file-transfer capabilities.
In practice, this includes setting aside specific space for DOD-related projects, providing badges and escorts to visitors, creating a log where visitors sign in and out, as well as protecting all locks, badges and other physical protections.
System & Communication Protection
The fourth CMMC 2.0 domain relevant at Level 1 is system and communication protection. The capacities and practices relevant at Level 1 fall under controlling communications at system boundaries. Here’s more detail on these specific practices.
Control Communications at System Boundaries
To control communications at system boundaries, organizations must monitor, control and protect organizational communications like information transmitted or received by information systems. The monitoring, controlling and protecting must take place at external boundaries and relevant internal boundaries within information systems.
Organizations must also implement subnetworks for publicly accessible system components that are physically or logically separated from internal networks. This practice is required so that there’s clear separation between public and internal systems.
System & Information Integrity
The fifth and final domain relevant under Level 1 within the CMMC 2.0 framework is related to system and information integrity. Here’s more on the specific requirements under this domain.
Identify and Manage Information System Flaws
CMMC 2.0 requires organizations to identify, report and correct information and information systems flaws in a timely manner. There must be a process in place for security patches and firmware updates.
Identify Malicious Content
Organizations must also identify malicious content via three specific processes.
First, organizations must provide protection from malicious code at appropriate locations within organizational information systems. This can be completed by deploying anti-malware to reduce the impact of any malware within an organization’s boundary.
Additionally, any organization within the DIB must also update malicious code protection mechanisms when new releases become available. Organizations can best meet this requirement by automating the signature and definition update for continuous protection.
Finally, contractors and others in the DIB must also perform periodic scans of information systems and real-time scans of files from external sources as files are downloaded, opened or executed. This means scanning systems periodically for malware, and ensuring that anti-malware scans are conducted by systems that interact with outside objects like emails, file downloads, thumb drive usage, etc.
.webp?width=1200&height=456&name=CMMC%202.0%20Key%20Changes%20(1).webp)
Source: https://www.acq.osd.mil/cmmc/about-us.html
Be Prepared With Sharetru
The ever-changing world of regulations and requirements for contractors working with the U.S. government is difficult for any organization to keep up with. At Sharetru, we keep up with these dynamic regulations and requirements so that you don’t have to. You’ll see the latest requirements reflected in our products when you need them. We secure your data away from your environment. We do so by encrypting the data in transit and at rest, and by hosting in a government-authorized FedRAMP data center.
We’ve seen in the past the government’s willingness to enforce the False Claims Act as needed to promote compliance. When contractors started signing DFAR contracts that required compliance with NIST 800-171, self-attestation was accepted. But, starting in 2020, the government started looking more closely at compliance and self-attestation was no longer enough. Expect the same arc for CMMC 2.0 compliance and enforcement. You can start preparing by following the outlined guidance above to meet Level 1 compliance.
What contractors and others in the DIB need is a good partner that can assist with compliance and general cybersecurity. Are you one of the many organizations trying to navigate the DOD’s changing CMMC requirements? Get in touch with us to talk about your cybersecurity needs.



.webp?width=1200&height=456&name=CMMC%202.0%20Key%20Changes%20(1).webp)
