The evolution of multi-factor authentication (MFA) is like that from the turning rotary phone, to the first mobile phones, and then the smartphones we use today. The ever-changing landscape of threats and best practices has led to constant innovation in authentication. The MFA we have today is vastly different from that of the ’90s when the earliest form of two-factor authentication (2FA) was invented and patented by AT&T.
2FA is just as the name implies: in addition to a password, an additional factor of authentication must be used to ensure the users' identity. This is especially true when it comes to your personal information (PII) or your organization’s proprietary information (PI). As we all know, a password is only as strong as the person using it, and to remember a password a user may tend to make it something easy like password123! or write it down and stick it to the back of their keyboard. This makes the idea of adding a second form of authentication very appealing as it could drastically decrease the risks associated with weak password policies and poor security practices. In fact, this has been proven to be highly effective at stopping cyber attacks using username and password combinations.
Multi-Factor Authentication (MFA) Assurance Levels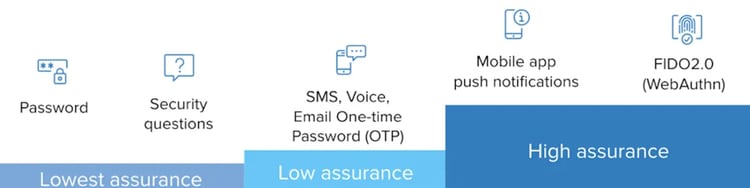
Unfortunately, cybercriminals are constantly evolving and finding new ways to steal login credentials and the data those credentials protect. To properly mitigate risk and keep sensitive information safe organizations need to do more than the traditional layers of defense. As we reviewed in our last blog post, multi-factor authentication (MFA) mitigates risk by requiring additional layers of authentication like something the user knows, has, and is. MFA is not only more secure – it also creates a more user-friendly experience because your users have confidence they are being protected.
In this blog, we want to go beyond the multi-factor authentication overview and look deeper into one of the most used types of MFA called One-Time Password (OTP) and the two primary methods: Time-Based One-Time Passwords (TOTP) and Hash-Based One-Time Passwords (HOTP).
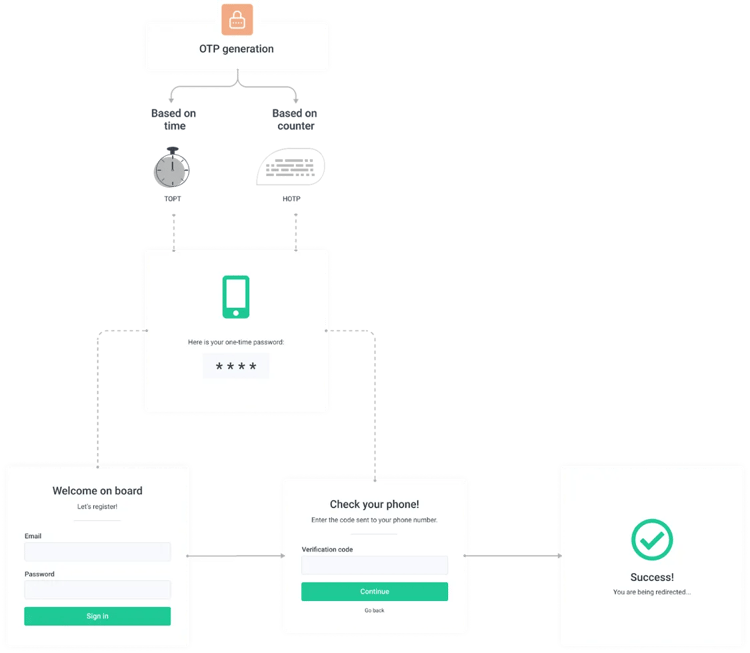
What is a One-Time Password (OTP) and How Does it Work?
OTP is a subcategory of MFA and, as the name suggests, can only be used one time. This means that even if the password (sometimes referred to as a passcode) ends up in the wrong hands it cannot be reused, and the next login by the user will require a completely different authentication code. These one-time passwords can be accessed in various ways such as apps, an SMS text message, a proprietary token – like a YubiKey, email, voice/phone call, and more!
For this reason, OTPs are often used in conjunction with a username and password login as an additional security requirement for users (or multi-factor authentication). Many organizations see OTP as an important part of a secure foundation for strong authentication.
TOTP vs HOTP Authentication
Advantages + Disadvantages of OTP
Like anything else, there are both pros and cons to not only implementing a one-time password solution but also to the various one-time password solutions themselves. First, we'll take a look at the advantages and disadvantages of OTPs themselves, and then look at some of the various types of OTPs available, and which ones stand out amongst the crowd.
Advantages of One-Time Passwords
- One-time passwords (OTPs) are single-use. The single-use password changes with each login attempt the risk of an account being hacked is drastically reduced.
- One-time passwords (OTPs) that are randomly generated provide exponentially more security than user-created passwords. Humans are very likely to use the same password across multiple accounts – personal and business. This oversimplification is typical because it is easier for the user to remember which increases security risks.
- Integrating One-time passwords (OTPs) makes it difficult for employees to share username and login credentials internally which makes it less likely the credentials could be obtained and used by hackers.
- One-time passwords (OTPs) remove the need for memorization altogether since the OTPs are randomly generated by some sort of authenticator app, SMS, voice, email, or physical token.
Disadvantages of One-Time Passwords
- User acceptance when implementing OTPs can have its challenges. The less tech-savvy users may find the process inconvenient, unnecessary, or confusing. This creates more work for IT teams by requiring additional explanations. Even users who appreciate and understand the security benefits of OTPs may end up frustrated or annoyed with the process if you don't allow OTP methods they are familiar with. These users prefer using an OTP delivery method that works with their mobile devices (which they are fess less likely to misplace or lose) such as mobile apps, SMS, or email.
- If your organization uses hardware tokens for OTP such as a key fob, there’s always a probability the token might be misplaced or lost by a user in your organization. The results can be costly because the hardware is not cheap, and the user may be unable to perform their job functions until the token is replaced. Additionally, if someone else gets their hands on the hardware AND has the employee’s login credentials the consequences could be immense.
- Possible delays in receiving an OTP via SMS or email. For example, email filters may send the code to SPAM.
Two Main Types of OTPs – HOTP & TOTP
As we mentioned in the introduction, there are two main types of OTPs – hash-based one-time passwords (HOTPs) and time-based one-time passwords (TOTPs). Both use two inputs to generate the OTP code: a secret key or seed, and a moving factor. The secret key/seed is a static value that’s created when you establish a new account on the authentication server. While the secret key/seed doesn’t change, the moving factor changes each time a new OTP is requested. How the moving factor is generated is the big differentiator between HOTP and TOTP. Next, we will review the differences between these from a security perspective, and which is more recommended.
Hash-Based One-Time Password (HOTP)
HOTP is available through open-source software. It was developed by the Initiative for Open Authentication (OATH – not to be confused with OAUTH) and published as an informational IETF RFC 4226 in December 2005. OATH developed its method of OTP to overcome the firm grip RSA Security had on the market for OTP authentication with its patented TOTP technology.
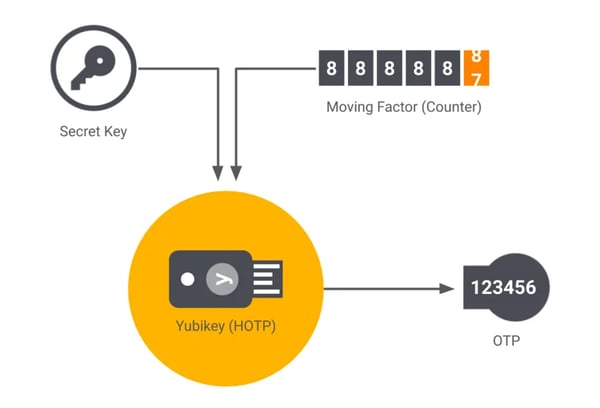
The “H” in HOTP comes from “hash-based message authentication code (HMAC).” HMAC-based One-time Password algorithm (HOTP) is an event-based OTP where the moving factor in each code is based on a counter, that is activated and incremented with each event. HOTP depends on two pieces of information:
- Secret Key/Seed: This secret key is only known by the users’ token and the server that validates submitted OTP codes.
- Moving Factor: The moving factor in an event-based OTP is a counter (counting the number of OTPs generated). The counter is stored in the token, on the server. The counter in the token increments when the button on the token is pressed, while the counter on the server is incremented only when an OTP is successfully validated.
To generate a HOTP, the secret key/seed and the moving factor aka counter are fed as an input into a one-way cryptographic hash function that outputs the OTP as a 160-bit hash code that is then reduced to the 6 (or 8) decimal code. The code that is then generated stays active until the user makes another request that is validated by the authentication server. Each time the code is validated, and access is granted the OTP generator and the server are synced. Yubiko’s Yubikey is an example of an OTP generator that uses HOTP.
Advantages
There are fewer advantages to HOTPs than TOTPs because TOTP is an evolved form of HOTP.
1. HOTP is More User Friendly
HOTP is not limited by an interval of time for the generated code to expire, and this adds flexibility as the user can enter the code whenever they choose to.
2. Event-Based OTP Algorithm
HOTP uses an event-based OTP algorithm with the moving factor being the event counter which is a time value. Since the OTP algorithm provides values that are short-lived based on the time-based variant – it can be more desirable when there is a need for enhanced security.
Disadvantages
1. HOTP is valid longer than TOTP
HOTP increments only change after authentication validation. This means that if the user does not access their account for a long period of time – the current OTP will be valid that entire time. This also means that potential attackers might have a longer amount of time to successfully infiltrate your systems.
2. HOTP May Encounter Sync Issues
The event counter in HOTP enables the potential for desynchronization between the server and the OTP token. For example, if the button on the OTP token is pressed too many times the value calculated by the server won’t align with the value on the token display. To counteract this the server needs to be able to accept previous and subsequent OTPs and all the accepted OTPs will create a validation window. This wider validation window increases the risk of an attacker breaking into a user’s account by brute forcing all the potential OTP values.
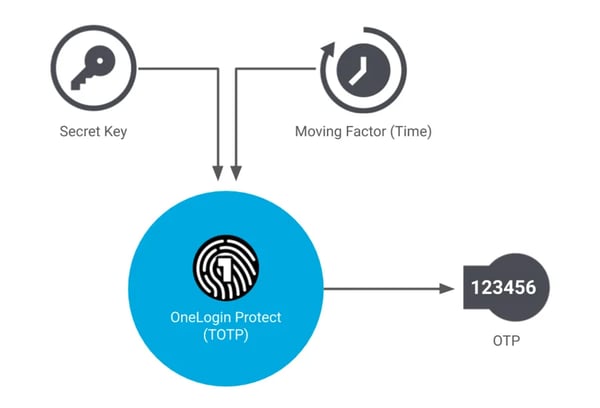
Time-Based One-Time Password (TOTP)
The time-based one-time password (TOTP) secret key/seed is static just like the HOTP, but the moving factor in TOTP is time-based (hence the name). The TOTP algorithm populates an OTP using a time counter – instead of a running counter – as the second input. The time counter is calculated by dividing the current Unix time by the timestep value. A timestep is a pre-set lifetime of an OTP, and in this case, is the amount of time that each password remains valid (typically for 30 or 60 seconds, but can be up to 120 seconds). The secret key/seed and the timestep are fed into a cryptographic hash function that outputs an OTP. If the password isn’t used within that allotted timestep, it becomes invalid, and a new OTP request must be made.
FUN FACT
The first TOTP authentication system was developed, patented, and marketed by RSA Security. Later, the Initiative for Open Authentication (OATH) developed its own variant of TOTP which it made freely available.
Advantages
1. TOTP is More Secure
TOTPs tend to be more secure because they are only valid for a specific period. The extra criteria required to be met greatly increase the security.
2. TOTP Offers Flexibility with Various Token Options
A TOTP authenticator can be embedded in both dedicated hardware tokens as well as implemented in software, typically as a mobile application such as Google Authenticator. By implementing it in software (also known as a software token) you avoid the costs associated with hardware manufacturing, distribution, inventory, and maintenance.
3. Internet Connection is Not Necessary
TOTP codes can be generated and accepted offline if the devices have the same secret key/seed and are in sync. This allows them to individually create TOTP codes and compare them against each other.
Disadvantages
1. TOTP Can be Phished and Stolen
Because of the nature of TOTP, it is possible (though unlikely) for a real-time phishing attack to occur. For example, an attacker could impersonate the system requesting the code. When the user enters their real code into the fake system, the attacker can then use the real code to log in to the real system. This can also happen using social engineering and man-in-the-middle traffic sniffing – where the attacker will read the code from the traffic.
2. TOTP Uses a Shared Secret/Seed
It is not a recommended security practice to use shared secrets/seeds. Shared secrets cannot be provided as a hash or with a cryptographic salt. Meaning it is likely stored in plaintext form, on the provider's server. This leaves all the shared secrets for all the TOTP generators, for all customers, in the service provider’s control. If a hacker gains access to both the password AND the shared secrets database, these secrets get stolen the cyber criminals can populate the codes without the end-users ever knowing.
3. TOTP is Dependent on a Device
TOTP generators are tied to a user’s device (ex: hardware token or mobile device). If this device is stolen, lost, or malfunctions, a service provider must re-issue a TOTP authenticator. Until this can be completed, providers typically fall back on less secure methods such as passwords and SMS codes.
HOTP vs TOTP – What is the Difference?
Either of those methods is better than not using multi-factor authentication (MFA) and as we reviewed above, they both have advantages and disadvantages – but what really matters? Well – that is up to your business needs.
TOTP is the newer OTP method and is easier to implement and has more flexibility for OTP delivery, while also keeping your organization more secure. However, it is important to note that because of the time-based element there is the potential for time-drift (the lag between the password creation and use). For example, if the TOTP is not entered right away there is a chance it will expire before it is entered. If this happens the server must account for it and ensure the user can try again without being locked out automatically.
HOTP has no time-based limitation making it slightly more user-friendly. However, since there may be a longer time window that the HOTP is valid, HOTP is more vulnerable to brute force attacks. There are some forms of HOTP that account for this weakness and include a time-based component to their code. This capability muddies the water a bit when comparing TOTP and HOTP.
Choosing the Right OTP Method
The use of one-time passwords (OTPs) has proven to bolster security by reducing fraud, compromised accounts and more. Most IT professionals agree that the additional effort required to implement OTPs is worth it for peace of mind.
If you are analyzing the differences between TOTP and HOTP from a security perspective – TOTP is the clear winner. There are more choices in delivery methods with TOTP, and while both TOTP and HOTP can be delivered using hardware or software tokens, the most notable OTP methods are specifically designed for TOTP. These TOTP-only methods include SMS, e-mail, and/or authenticator apps.
Regarding the traditional hardware key fob OTP tokens – these are getting smaller and thus more manageable. Microcosm has now introduced the OTP Card - a credit card sized OTP token with EPD display. It is obvious how these cards could be more convenient since they can be easily stored with other valuable cards.
Is OTP Secure?
OTP-based MFA can bolster password security. However, it is important to remember that the security of OTP (TOTP/HOTP) depends on how it is implemented. Many ways of implementing OTP – such as sending a code via SMS or email – are less secure than app-based OTP. For example, NIST has deprecated the use of SMS-based OTP for federal systems since 2017, and email-based TOTP provides little protection if the account and email account share a password.
Additionally, HOTP and TOTP are still vulnerable to phishing attacks. While MFA adoption is on the rise, cybercriminals have evolved their tactics to steal OTPs in various ways.
Share with Confidence with Sharetru
Sharetru's secure file transfer solution options and essential control features include various authentication methods and security features to fit your business needs, and different methods of OTP can be aligned to different users. When TOTP is integrated in conjunction with Sharetru’s account lockout policy feature which can be customized by an administrator, your organization has the tools to build a strong authentication policy in relation to transfers. Our platform is designed with security and compliance in mind for businesses of all sizes. Learn more about our different plans and features such as MFA, unlimited users, dedicated servers, automation rules, activity logs, consistent security controls, SSO integration, and more.
If you work within an organization that often needs a secure method for storing and sharing sensitive files — one that works efficiently and helps streamline day-to-day operations across departments — Sharetru can deliver an affordable, effective solution. If you have HIPAA, GBLA, or other compliance needs, schedule a demo with us today!






